Attack Vactor Scheme involving several hacking techniques, here I use two ways to gain access to the target computer.
We will do the buffer overflow hacking technique on BigAnt server, The following is an explanation
- Install applications BigAnt server on the komputer target and run the application hacking on the lab
- We will make and send fuzzer to the application containing the value to make crash
- If successful then the target will be opportunities for remote start
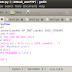
- Below is fuzzer to be sent to the target application
- If it works then we obtain the permissions on the same target
Next, we will perform metasploit hacking techniques
- We need IG on target, now i will try to get IG use nessus, look the pick IG with nessus.
- After open terminal and write msfconsole
- Next step we will need list exploit for get file target, write show exploit
- The next step will be to determine which exploit we use

- Show us the options to see the contents of the file
- The next step we make LHOST, LPORT, RHOST
- And it's time to exploit
- Checking results
We will do the buffer overflow hacking technique on BigAnt server, The following is an explanation
- Install applications BigAnt server on the komputer target and run the application hacking on the lab
- We will make and send fuzzer to the application containing the value to make crash
- If successful then the target will be opportunities for remote start
- Below is fuzzer to be sent to the target application
- If it works then we obtain the permissions on the same target
Next, we will perform metasploit hacking techniques
- We need IG on target, now i will try to get IG use nessus, look the pick IG with nessus.
- After open terminal and write msfconsole
- Next step we will need list exploit for get file target, write show exploit
- The next step will be to determine which exploit we use

- Show us the options to see the contents of the file
- The next step we make LHOST, LPORT, RHOST
- And it's time to exploit
- Checking results
















0 comments:
Post a Comment