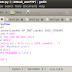
Ok i'm back again for share my report about Sleuthkit Unallocated Extraction & Examination.
first about sleuthkit, we must installation sleuthkit, simple installation we can find tutorial from google..in there we can get tutorial about how to steps installation sleuthkit.
SleuthKit is a collection of shell program for forensic analysis,
SleuthKit, in general, consists of two parts, namely the file system and media tools
management tools. File system is useful tool to analyze the file system.
ok we go to my report, lets see the picture...

sorry my packet internet exhausted, so i will post pict report tomorrow....i'm so sorry for that
first about sleuthkit, we must installation sleuthkit, simple installation we can find tutorial from google..in there we can get tutorial about how to steps installation sleuthkit.
SleuthKit is a collection of shell program for forensic analysis,
SleuthKit, in general, consists of two parts, namely the file system and media tools
management tools. File system is useful tool to analyze the file system.

sorry my packet internet exhausted, so i will post pict report tomorrow....i'm so sorry for that