Okay, now we will learn a little about the direct returns method, and how to exploit application warftp.
lets see, what we need next ?
- Backtrack 5
- Metasploid Framework
- VirtualBox Windows XP Sp2
- Fuzzer
- OllyDbg
- WarFTP
- If you need a coffe, please make for a more relaxed..;)
Ok lets go to the steps,
Open Virtualbox Windows XP and the application WarFTP and make connections with BackTrack, if ready we must make script with python for run the Fuzzer,..ok lets see image :
and run this command...
next steps try to make writer at ESP, create script "war3.py"
ok now we must get jump ESP, on ollydbg aplication menu view - executable modules - shell32.dll
after right click search for - command - write JMP ESP.....and see the result


ok now create payload that will be inserted into the buffer

options paylod
Generate and we have a payload..:)
last steps, create a new script in which there are payload, look d image bellow,
Compiler python war_payload.py at console......
after run fuzzer we will look WarFtp application not responding. it means fuzzer that contains the payload has been successfully exploit.
now open console and running talnet for access windows xp trough easy RM application..
---BoooM..:)---
lets see, what we need next ?
- Backtrack 5
- Metasploid Framework
- VirtualBox Windows XP Sp2
- Fuzzer
- OllyDbg
- WarFTP
- If you need a coffe, please make for a more relaxed..;)
Ok lets go to the steps,
Open Virtualbox Windows XP and the application WarFTP and make connections with BackTrack, if ready we must make script with python for run the Fuzzer,..ok lets see image :
after writing the script, run this command on terminal
this command is to asceltain whather the WarFtp is acttual running.
now we will running the script "war.py" at console
after Fuzzer process then warFtp will error......this is because user configuration file generated by warftp be broken. Fuzzer try to send data, fuzzer try to send as much data as 1000 byte via user command.we will see ollydbg, what is result now ? there has been a crash in the system registry
next step, now we open warftp at ollydbg and we make a Fuzzer with name "war1.py" lets see the script war1.py.....and this, we must create pattern as 1000 byte for get value buffer
if ready the script we run Fuzzer "war1.py"
we will see ollydbg, what is result now ? value from registry on the memori warftp aplication server have fully charged with string pattern.
next step we must get pattern offset from address EIP and value ESP.....
./pattern_offset.rb 32714131
485
and
./pattern_offset.rb q4Aq5Aq
493
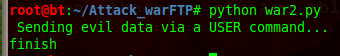
next, create new fuzzer with name "war2.py"
and run this command...
next steps try to make writer at ESP, create script "war3.py"
ok now we must get jump ESP, on ollydbg aplication menu view - executable modules - shell32.dll
after right click search for - command - write JMP ESP.....and see the result


ok now create payload that will be inserted into the buffer

options paylod
Generate and we have a payload..:)
last steps, create a new script in which there are payload, look d image bellow,
Compiler python war_payload.py at console......
now open console and running talnet for access windows xp trough easy RM application..
---BoooM..:)---

























0 comments:
Post a Comment