After a few days I tried to exploit the easy RM application and having problems,but now I will try to explain how to exploit easy RM application using perl language in Backtrack...
Ok, this is step by step......
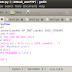
We have create new fuzzer and save file with name "crash.pl" on Backtrack...Example file name: crash.pl, ok time to write the script.
if u finish writing the script, u have open console on backtrak and find the file to compiler,
example :
root@bt : cd ./Attack_RM/ >>> Enter
root@bt : Attack_RM/ perl crash.pl >>> Enter
look ur file, now we have creat 1 file with name crash.m3u..
next step, open virtualbox and run windows xp sp2 in backtrack, if have ready... open OllyDbg and open easy RM in OllyDbg after running or play,
after RM have running, we have open file "crash.m3u"
we will see the program have crash...means file fuzzer has been successfully running...
next, we create new fuzzer again, name file "crash30000.pl"...look at image bellow and write the script....
If finish, going to console and run the fuzzer
open ollyDbg and RM again, and running the file m3u again, look the image wat happend with the RM ?
Next steps same with previous steps, create fuzzer "crash_pc.pl"
but before we must create a data dummies that have been structured or pattern_create.
if u have find patter_create.rb 10000, copy the pattern and paste to script..
And now we must run fuzer "crash_pc.m3u" to RM and look the application,
Next, we must find offset of EIP
Next steps, folow the script.....
Look image bellow, ESP data has changed with 1000 byte character C, and EIP has changed to 42424242..
Next step, create new fuzzer with name "test.pl" which contains shellcode..
Next step, create new fuzzer with name "test1.pl" which contains $shellcode..
Result fuzzer "test1.m3u"
After seeing the results, don't close the application, but we go to ollyDbg look ESP and right click follow dumb, we will result ESP space. after we go to ollyDbg menu - Executable Modules, look new panel, in here i used MSRM Coodec02.dll files to find JMP ESP.
If u have click the file, u must find address Jump ESP...look the image bellow,
 Next steps,
Next steps,
Look the script fuzzer "test2.pl".
Ok final steps,
Create new fuzzer "test3.pl and find paylod for input to the script. look the image for u steps.
If u want get code payload u must open console and open msfweb...
Ok, this is step by step......
We have create new fuzzer and save file with name "crash.pl" on Backtrack...Example file name: crash.pl, ok time to write the script.

if u finish writing the script, u have open console on backtrak and find the file to compiler,
example :
root@bt : cd ./Attack_RM/ >>> Enter
root@bt : Attack_RM/ perl crash.pl >>> Enter
look ur file, now we have creat 1 file with name crash.m3u..
next step, open virtualbox and run windows xp sp2 in backtrack, if have ready... open OllyDbg and open easy RM in OllyDbg after running or play,
after RM have running, we have open file "crash.m3u"
we will see the program have crash...means file fuzzer has been successfully running...
next, we create new fuzzer again, name file "crash30000.pl"...look at image bellow and write the script....
If finish, going to console and run the fuzzer
open ollyDbg and RM again, and running the file m3u again, look the image wat happend with the RM ?
Next steps same with previous steps, create fuzzer "crash_pc.pl"
but before we must create a data dummies that have been structured or pattern_create.
if u have find patter_create.rb 10000, copy the pattern and paste to script..
And now we must run fuzer "crash_pc.m3u" to RM and look the application,
Next, we must find offset of EIP
Next steps, folow the script.....
Look image bellow, ESP data has changed with 1000 byte character C, and EIP has changed to 42424242..
Next step, create new fuzzer with name "test.pl" which contains shellcode..
Look the result fuzzer "test.m3u"
Next step, create new fuzzer with name "test1.pl" which contains $shellcode..
Result fuzzer "test1.m3u"

After seeing the results, don't close the application, but we go to ollyDbg look ESP and right click follow dumb, we will result ESP space. after we go to ollyDbg menu - Executable Modules, look new panel, in here i used MSRM Coodec02.dll files to find JMP ESP.
If u have click the file, u must find address Jump ESP...look the image bellow,
 Next steps,
Next steps,Look the script fuzzer "test2.pl".
Ok final steps,
Create new fuzzer "test3.pl and find paylod for input to the script. look the image for u steps.
If u want get code payload u must open console and open msfweb...



























0 comments:
Post a Comment